Data Loss Prevention (Spirion)
What You Need to Know
Spirion is a program that locates Protected Level 1 data in files such as Word, Excel, PDF, and other common file types. In addition to locating Protected Level 1 data, Spirion can perform actions on locations that contain Protected Level 1 data. Such actions include the ability to Shred (securely delete) and Redact (mask specific sensitive data) in order to protect yourself (or others) from identity theft.
What You Need to Do
Get Started
After a scan, a results window will pop up as shown here:
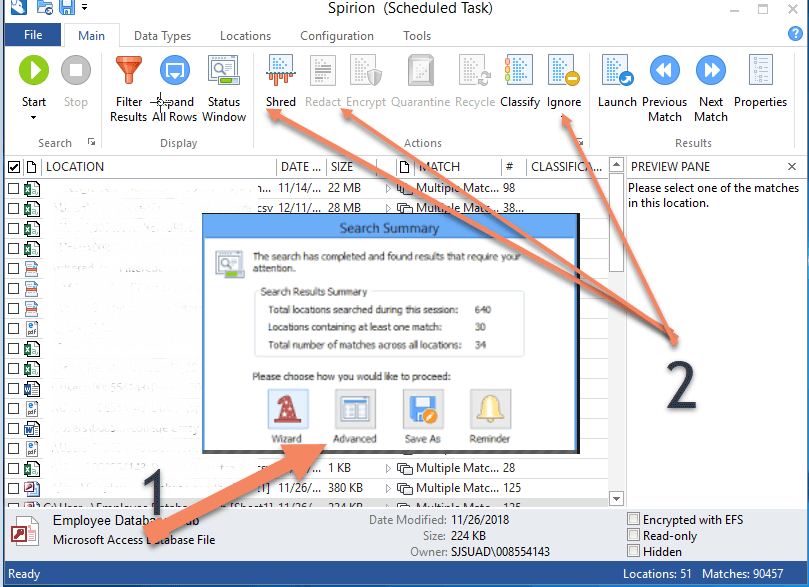
- Click “Advanced”
- Go through each match and choose between the following:
- Shred, which securely and permanently deletes the file. This is a permanent action that cannot be undone.
- Redact, which replaces or “masks” the sensitive data with dummy data. This is a permanent action that cannot be undone.
- Ignore, which is for false positives -- your ignored matches will be remembered and will not need to be repeated in subsequent scans, in most instances.
Please note: Spirion was formerly known as "Identity Finder" - these terms are interchangeable.
This tool will find and assist you with protecting Level 1 Protected Data (PII), or other data elements that can be used for identity theft. This data would allow someone to steal your identity by obtaining them individually, or by using them in combination with each other. Such data includes:
- Social Security numbers
- Credit card numbers
- Password entries
- Bank account numbers
- Driver’s License numbers
- Passport numbers
- Australian, Canadian and UK ID numbers
The types of files that Spirion searches for are Microsoft (Word, Excel, Access, PowerPoint, etc.) Adobe (PDF), text files, web files, compressed file and other common file types that are more likely to store Level 1 data. Such data can come from a broad range of activities and records including the following:
- Old Class Rosters
- Old Student Time Sheets
- Demographics data and records requested by federal agencies or professional organizations
- Human Resource Records
- Student Reporting
The Information Security Office recommends destroying any confidential information which is no longer needed.
Frequently Asked Questions
Where Does Spirion Search?
Spirion will search through specific folders in your computer's hard drive for Protected Level 1 data. These include, but are not limited to:
- Local user folders (Documents, Desktop, Downloads, Music, etc.)
- Web Browsers (saved passwords, browser cache, Favorites/Bookmarks, etc.)
- Windows Registry
Spirion will not search certain folders reserved by the Operating System like C:\Windows\, as these are typically write-protected and require admin privileges to access. San Jose State University and its employees are responsible for PII data for individuals that is collected and stored. If you have a question about the data you are storing, and whether you should be storing it, please ask your manager.
For future reference, our Quick Scanning Guide can assist you in launching, searching, shredding, ignoring, and saving results.
Additional Resources
A Few Items To Be Aware Of
The scan will be scheduled for after-hours, initially on a bi-weekly basis, and later as we more fully deploy, to once a month. If the scan is not successful because the user is not logged in, or the computer is not on, the scan will occur at the next user login.
Google Drive is in scope for scanning.
The preview pane on the right shows details for matches found.
It may be useful to press “Collapse All Rows” to show a list of Locations (files), rather than each specific Match. The number of locations will be much fewer than the number of total Matches.
Continue to go through each Match until you’re done with all Matches.
CFA & CSUEU Review
CSU labor relations and system-wide Information Security reviewed the Spirion deployment, and has recognized the importance and the value of this implementation to our security process.
CSUEU Approval [pdf]: 3/3/14, “The parties acknowledge that CSU is required by law and CSU policy to monitor and protect the security of data used and stored on its systems and acknowledge the importance of working together to ensure the security of the data.”
CFA Approval [pdf]: 7/21/14, “The parties acknowledge the importance of working together to ensure the security of data used and stored on CSU system."
Policy
ICSUAM Policy 8065.0 [pdf] - Information Asset Management from the Information Security Policy section of the Integrated CSU Administrative Manual
Support: Need Help or Have Questions?
For Spirion support, submit a help request.